Enumerating NFS Shares Port 2049 Posted on December 12 2020 by Harley NFS shares are not only common to come across during the OSCP and in capture the flag events like Hack The Box but theyre also common to see during internal pentest engagements. 23012381 - Pentesting CompaqHP Insight Manager.

Hack The Box Jail Walkthrough An Evaluation On Stealthiness Folmer S Website
3632 - Pentesting distcc.
2049 port hack tricks. Rsh use rhosts files and etchostsequiv for authentication. 23012381 - Pentesting CompaqHP Insight Manager. 3306 - Pentesting Mysql.
2049 - Pentesting NFS Service. This also makes it popular for CTF forensics challenges. 3389 - Pentesting RDP.
Port 2049 - NFS. 2375 2376 Pentesting Docker. 3389 - Pentesting RDP.
If the service is on its default port you can run this command to see what the filesystem is sharing. 3299 - Pentesting SAPRouter. You can try to exploit it.
80 WWW or HTTP standard web server port. 2049 - Pentesting NFS Service. The result of OR-ing a variable with a value that has n-th bit set is turning that n-th bit on.
3632 - Pentesting distcc. Part of Hacking For Dummies Cheat Sheet. Enumerating NFS Shares Port 2049 Posted on December 12 2020 by Harley in Enumeration Cheatsheets NFS shares are not only common to come across during the OSCP and in capture the flag events like Hack The Box but theyre also.
In your security tests be sure to check these commonly hacked TCP and UDP ports. Now includes Python scripting to automatically capture packets from the network using tshark. 69 tftp or Trivial File Transfer Protocol.
Low risk as a crack target but gives out way too much information and should not be run. Just type in the value below and start playing. But OR-ing it with 1 changes it to 1 if it wasnt already.
Network File System NFS - remote filesystem access RFC 1813 RFC5665. Response is highly important Collection of Web-Shells Guides - Hacktricks bypass file upload Hackers Grimoire Book We can use hacktricks first try out every single extensions and then try double extensions. A commonly scanned and exploited attack vector.
These methods relied on IP addresses and DNS Domain Name System for authentication. Lean how to automate your captures and learn how to hack the network using Python and Wireshark. 4369 - Pentesting Erlang Port Mapper Daemon epmd 5353UDP Multicast DNS mDNS 54325433 - Pentesting Postgresql.
3632 - Pentesting distcc. However spoofing IP addresses is fairly easy especially if the attacker is on the local network. TheBAHdotCOM presents their very first Rush 2049 videoCOM decided to go retro this week and play a few Nintendo 64 games including Mario Kart Mario Party 3.
Yum install nfs-utils nfs-utils-lib -y systemctl enable nfs-serverservice Beofre starting nfs service start rpc bind service systemctl start rpcbind systemctl start nfs-serverservice systemctl status nfs-serverservice. The NSA wrote a guide to these hiding places in 2008 titled Hidden Data and Metadata in Adobe PDF Files. NFS service Port Number.
Or use Burp Suite to bruteforce Cyber Kill Chain cont Bypass File Upload Download PHP pentest monkey rev shell rev shell with GIF89a. This post intends to serve as a guide for enumerating a NFS share and different opportunities for abusing their functionality. PDF is an extremely complicated document file format with enough tricks and hiding places to write about for years.
What port does Night Owl use. 1150Use Local IP Address to connect to DVR when youre connected to the same network as the DVR Router address192168. Hack network protocols like DTP VTP STP and DHCP using Ethical hacking tools included in Kali Linux.
Furthermore the rhosts files were stored in users home directories which. 2049Use the Web port when connecting with Internet ExplorerMedia Port9000Use the Media port when connecting with a computer or laptopDNS1. The 2048 Hack Version lets you set the value of the generated tiles allowing you to beat all of their scores.
Its because OR-ing any value with 0 leaves the value the same. 23012381 - Pentesting CompaqHP Insight Manager. 3690 - Pentesting Subversion svn server 4369 - Pentesting Erlang Port Mapper Daemon epmd 5000 - Pentesting Docker Registry.
3306 - Pentesting Mysql. LAN only if really really needed. BACKDOORS Empire ICMPsh Merlin Salseo X.
4369 - Pentesting Erlang Port Mapper Daemon epmd 5353UDP Multicast DNS mDNS 54325433 - Pentesting Postgresql. TCP port 21 FTP File Transfer Protocol TCP port 22 SSH Secure Shell TCP port 23. 3299 - Pentesting SAPRouter.
To Install NFS packages and utils in NFS Server use below commands. Read 2049 - Pentesting NFS service to learn more about how to test this protocol. 2049 - Pentesting NFS Service.
Enumerating NFS Shares Port 2049 NFS shares are not only common to come across during the OSCP and in capture the flag events like Hack The Box but theyre also common to see during internal pentest engagements. Common ports such as TCP port 80 HTTP may be locked down but other ports may get overlooked and be vulnerable to hackers. Network file system This is a service used so that people can access certain parts of a remote filesystem.
This bit hack combines the same 1. If this is badly configured it could mean that you grant excessive access to users. If you find the service NFS then probably you will be able to list and downloadand maybe upload files.
Normally port scanning is needed to find which port this service runs on but since most installations run NFS on this port hackerscrackers can bypass fingerprinting and try this port directly. Publication Risks and Countermeasures. 5353UDP Multicast DNS mDNS 54325433 - Pentesting Postgresql.
Alternatively you could also set the starting value to a strange number or a word and see what happens. CRYPTO Certificates Cipher Block Chaining CBC-MAC Crypto CTFs Tricks Electronic Code Book Padding Oracle RC4 - EncryptDecrypt X. 79 Finger used to provide information about the system and logged in users.
If you find the service ypbindrunning.

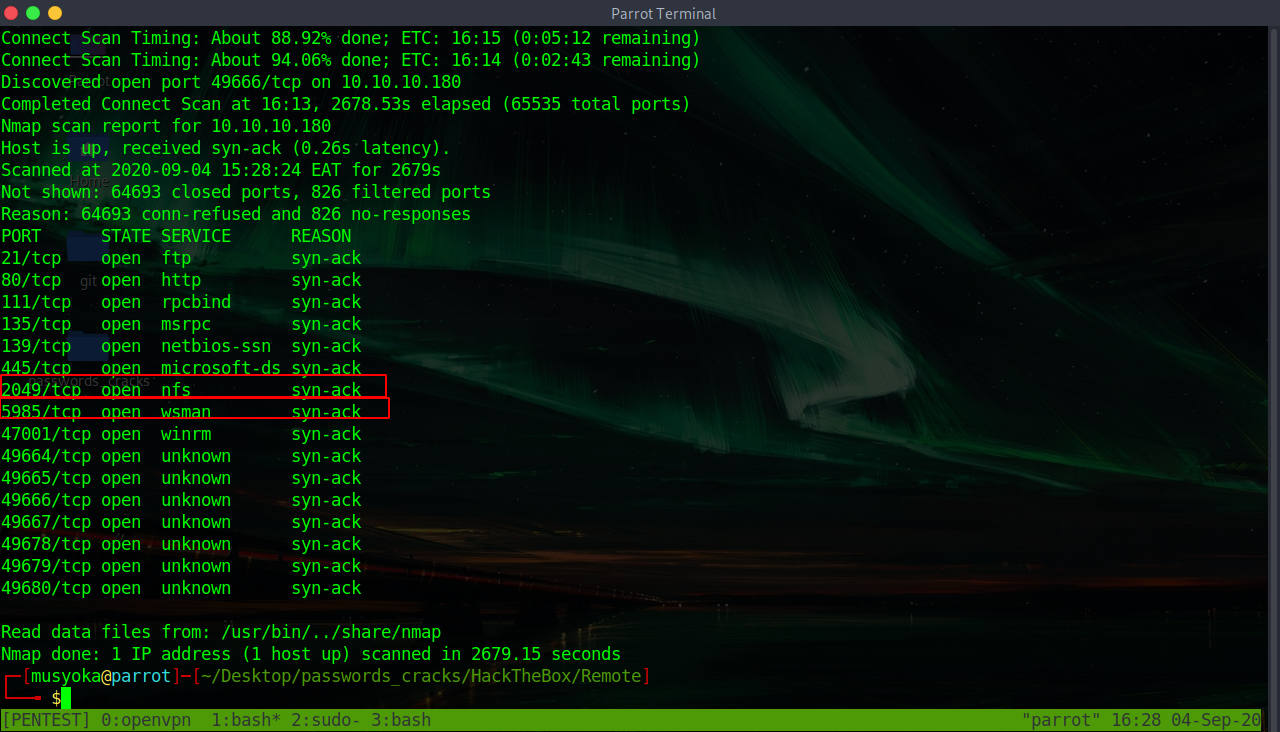
Remote Hackthebox Walkthrough Hello Guys Hackthebox Team Has Retired By Musyoka Ian Medium

Vmware Vi3 Network Communication Diagram Network Diagram Networking Computer Network

Phone Stand With Cable Routing Phone Phone Stand 3d Printing
Poking Holes In The Firewall Egress Testing With Allports Exposed Black Hills Information Security
Hacklab Vulnix Walkthrough Vulnix Is A Boot To Root Virtual By Dasagreeva Medium

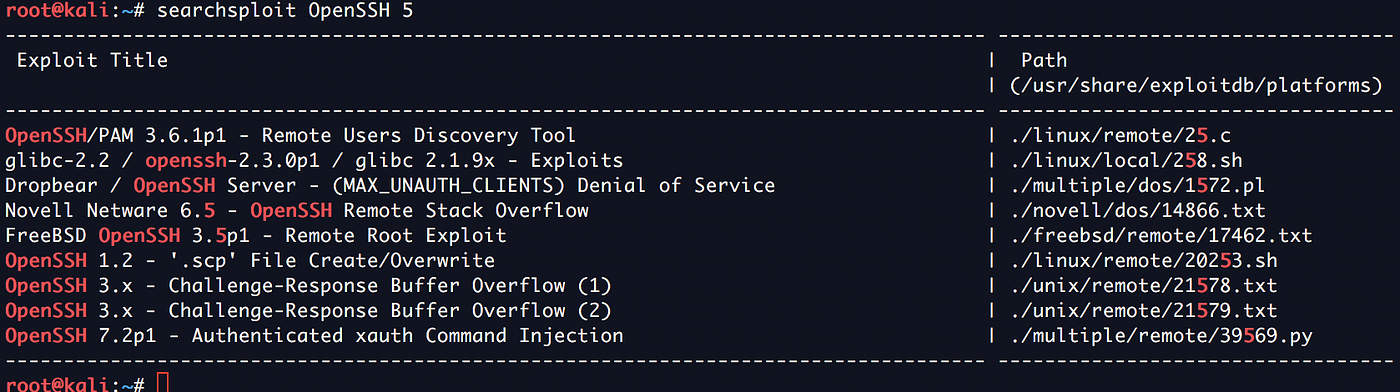
Top 10 Nmap Widely Used Commands Yeah Hub
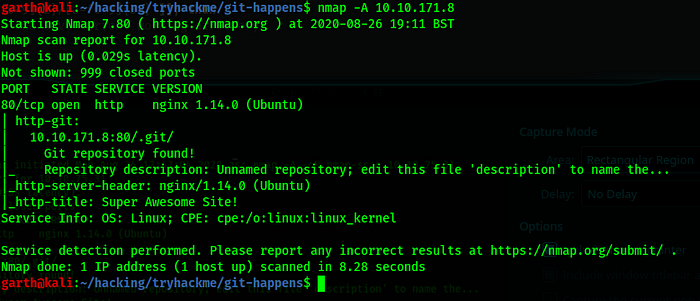
Try Hack Me Willow Walkthrough There Is Not A Lot Of Information About By Yebberdog Medium

Discover The Tools Used In The Mr Robot Television Show To Break Into Target Computers Then Download Play And Best Hacking Tools Web Design Programs Mr Robot

Nmap Parse Output V1 4 4 Releases Converts Manipulates Extracts Data From A Nmap Scan Output Cyber Security Manipulation Data Cyber Security

Amazon In Buy Logitech K230 Wireless Keyboard Online At Low Prices In India Logitech Reviews Ratings Logitech Keyboard Pc Laptop

Smb2 Capties Hackathon Root Apps It Network

Hack The Box Jail Walkthrough An Evaluation On Stealthiness Folmer S Website

Common Tcp Ip Ports And Protocols Poster Technology Posters Office Artwork Professional Art
Hacklab Vulnix Walkthrough Vulnix Is A Boot To Root Virtual By Dasagreeva Medium
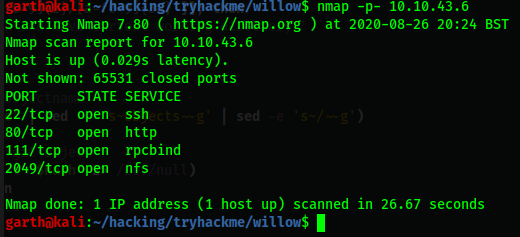
Try Hack Me Willow Walkthrough There Is Not A Lot Of Information About By Yebberdog Medium


ConversionConversion EmoticonEmoticon