The device will automatically reboot impacting network availability for other devices. A good way to determine this is to issue the command.
Dark Side 114 Exploiting Nfs What Is Nfs And How Can We Enumerate By Katlyn Gallo Dark Roast Security Medium
He was in Bad Lieutenant.

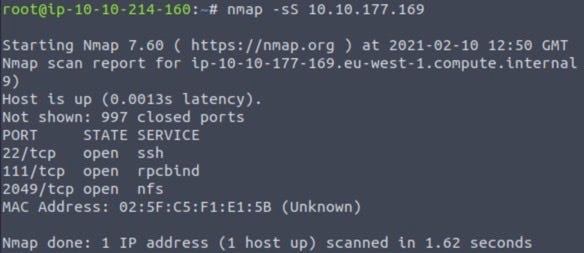
2049 port exploit. If this is badly configured it could mean that you grant excessive access to users. Vulnix Walthrough Vulnhub Vulnix is a challenging vulnerable VM you can download it from Vulnhub. Port 2049 - NFS.
This virtual machine is compatible with VMWare VirtualBox and other common. Guaranteed communication over port 2040 is the key difference between TCP and UDP. The Exploit Database is a repository for exploits and proof-of-concepts rather than advisories making it a valuable resource for those who need actionable data right away.
Hopefully the expectant results will look something like this. Note that for this exploit you need to first install nfs-common with apt-get-install nfs-common on your Kali Linux machine. Link 1 Daniel Murphy played for Binghamton in 2008.
Network File System NFS - remote filesystem access RFC 1813 RFC5665. 2062 2061 2060 2059 2058 2057 2056 2055 2054 2053 2052 2051 2050 2049 2048 2047 2046 2045 2044 2043 2042 2041 2040 2039 2038 2037 2036 2035 2034 2033 2032 2031 2030 2029 2028 2027 2026 2025 2024 2023 2022 2021 2020 2019 2018 2017 2016 2015 2014 2013. The Google Hacking Database GHDB is a categorized index of Internet search engine queries designed to uncover interesting and usually sensitive information made publicly.
TCP is a connection-oriented protocol it requires handshaking to set up end-to-end communications. Port Of Call New Orleans with Val Kilmer. The above command causes ssh on the client to take any request directed at the clients port 250 and forward it first through sshd on the server and then on to the servers port 2049.
The VM needs to be on the same network as the attacking machine as well. Since this is a fileformat exploit we will look. Normally port scanning is needed to find which port this service runs on but since most installations run NFS on this port hackerscrackers can bypass fingerprinting and try this port directly.
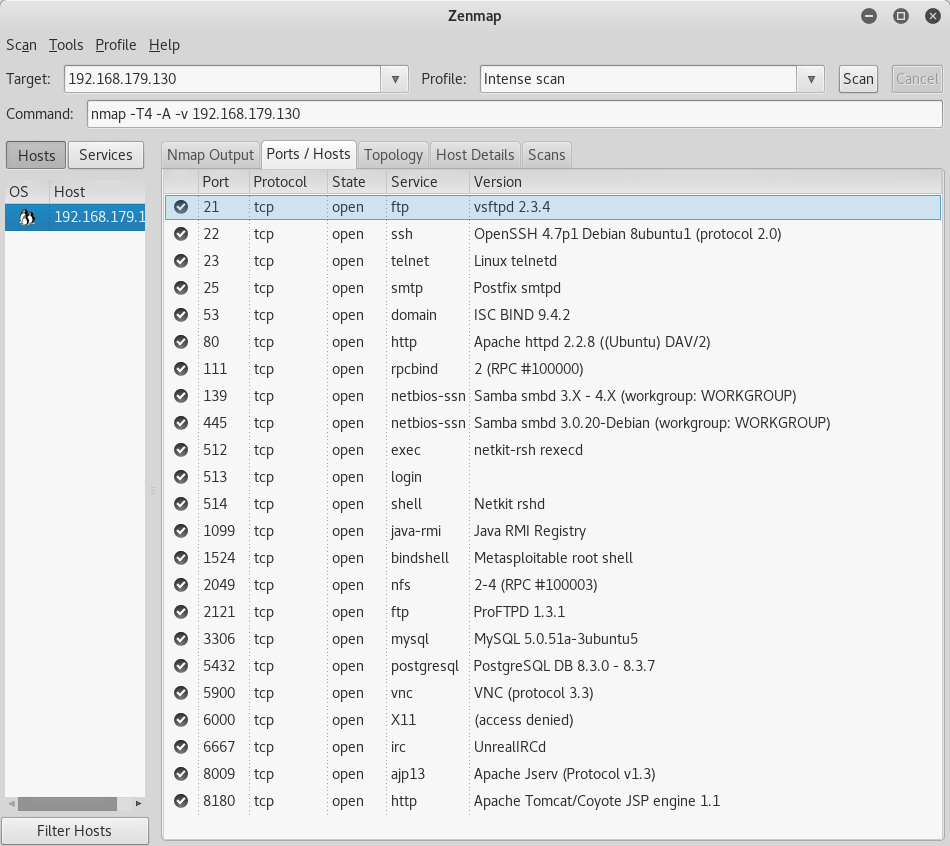
We will use the A-PDF WAV to MP3 Converter exploit. Vncviewer 1721692140 It turns out that the password is password and we have root privileges as well. An attacker must have network access to port 443tcp to exploit.
The rpcbind service redirects the client to the proper port number so it can communicate with the requested service. Use of NFS on a system can be determined if port 2049 is open this is a good indication but it doesnt actually prove any folders are being offered. Remote exploit for Multiple platform.
UDP port 2040 would not have guaranteed communication in the same way as TCP. Because protocol TCP port 2040 was flagged as a virus colored red does not mean that a virus is using port 2040 but that a Trojan or Virus has used this port in the past to communicate. This backdoor was present in the Unreal3281targz archive between November 2009 and June 12th 2010.
Nfs runs on port 2049 for both TCP and UDP. TCP is one of the main protocols in TCPIP networks. Network file system This is a service used so that people can access certain parts of a remote filesystem.
In 2011 he was a guest star on Extreme Makeover. Version 2 of this virtual machine is available for download and ships with even more vulnerabilities than the original image. When porting exploits there is no need to start coding completely from scratch.
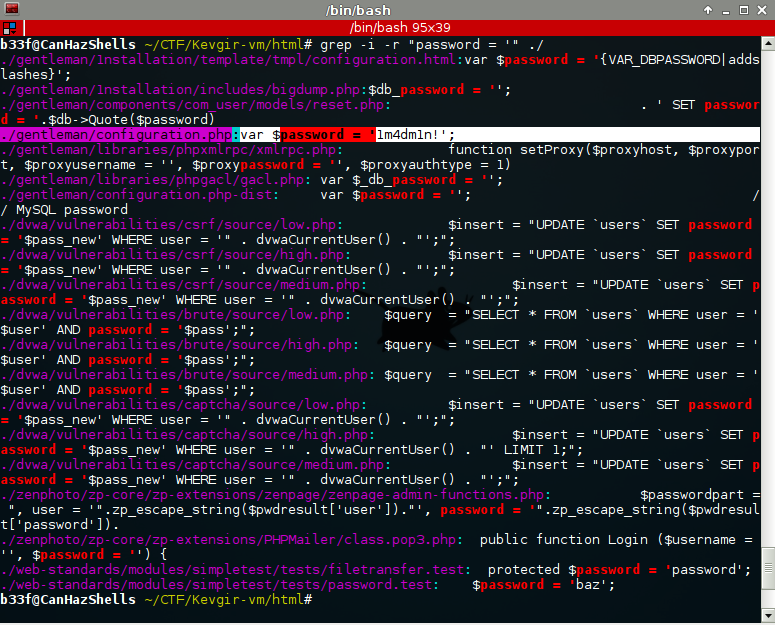
Get my OWASP course with 90 discount on UdemyUse coupon code. Rpcbind runs on port 111 for both TCP and UDP. Showmount -e IP_Address.
Splunk - Remote Command Execution. The Metasploitable machine is at 100027. Port 2049 - NFS.
Another guest star on the show was Xzibit. Start by checking out what network services are running - use the rpcinfo command to do that. The second line causes a similar type of forwarding between requests to port 251 on the client and port 32767 on the server.
Only when a connection is set up users data. I assume the VM is loaded correctly and DHCP successfully assigned it an IP. The web interface on port 443tcp could allow an attacker to cause a Denial-of-Service condition by sending specially crafted packets to the web server.
Home Edition for their Veterans Day episode. Ssh runs on port 22. If the service is on its default port you can run this command to see what the filesystem is sharing.
Port 6667 has the Unreal IRCD service running we will exploit is using a backdoor thats available in Metasploit. Moving on port 5900 I tried to connect it via VNC and tried the common passwords. Allowing the world to mount to the file system opens up Paradoras box to an unlimited amount of exploits.
Metasploitable 2 The Metasploitable virtual machine is an intentionally vulnerable version of Ubuntu Linux designed for testing security tools and demonstrating common vulnerabilities. This module exploits a malicious backdoor that was added to the Unreal IRCD 3281 download archive. 2049 - Pentesting NFS Service Basic Information It is a clientserver system that allows users to access files across a network and treat them as if they resided in a local file directory.
A commonly scanned and exploited attack vector. To begin well first need to obviously select an exploit to port over. TCP port 2049 uses the Transmission Control Protocol.
The Anti Hacker Alliance fights against Spammers Hackers CyberCrime Intruders Attackers Spam Gangs Internet Terrorists and Spam Support Mafias world wide. Thanks to Rebootuser for creating this fun challenge. There are many steps you can take to harden the NFS service however for this particular machine I just added iptables commands to block the Kali machines IP from.
We can see that there is an NFS service listening on port 2049. We can simply select a pre-existing exploit module and modify it to suit our purposes. Here is the tutorial for the exploit.
This will return information about open ports and RPC services. Rpcinfo -p 100027. Kilmer was in Top Gun with Tom Cruise who was in A Few Good Men with Kevin Bacon.

Tryhackme Vulnnet Internal Writeup

No Open Port Report In Deepexploit And Scan Show All Ports Open Issue 42 13o Bbr Bbq Machine Learning Security Github

Comprehensive Guide On Metasploitable 2

Linux Privilege Escalation Exploiting Nfs Shares Steflan S Security Blog

Comprehensive Guide On Metasploitable 2

How To Enumerate And Exploit Nfs Shares Ethicalhackingguru Com
Fuzzysecurity Game Over Canyoupwnme Kevgir 1

Hackthebox Remote Writeup Jackhack
Metasploitable Project Lesson 4 Exploiting A Mis Configured Nfs Share

Comprehensive Guide On Metasploitable 2
Metasploitable 2 Exploits And Hardening Guide

Hackthebox Remote Writeup Jackhack

Comprehensive Guide On Metasploitable 2
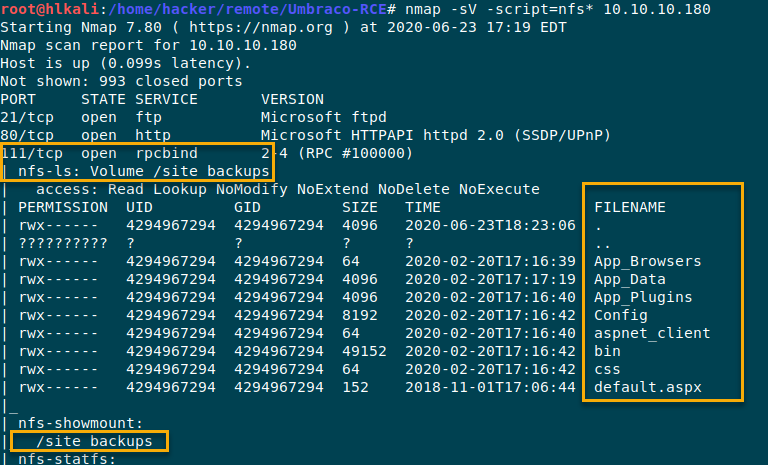
Hack The Box Remote 6 Htb Is A Platorm Which Provides A Large By Curls Medium

Hacking Metasploitable2 With Kali Linux Exploiting Ports 111 2049 Rpcbind Nfs Youtube

Comprehensive Guide On Metasploitable 2

Comprehensive Guide On Metasploitable 2


ConversionConversion EmoticonEmoticon